Penetration testing services
Our Penetration testing services discovers the internal and external attack surfaces and test its readiness against the latest advanced threats. The service will assess the potential impact of exploiting each discovered vulnerability and give recommended remediation. This will enable you to understand and significantly reduce your organization’s cyber security risk. The test report will give your organization and insight about vulnerabilities that can be exploited by attackers, provides independent assurance. In addition to that it supports compliance requirements
Methodology
Our methodology is based on the Open Source Security Testing Methodology Manual (OSSTMM) which defines the following
- Project scope
- Confidentiality and non-disclosure assurance
- Emergency contact information
- Statement of work change process
- Test plan
- Test process
- Reporting standard
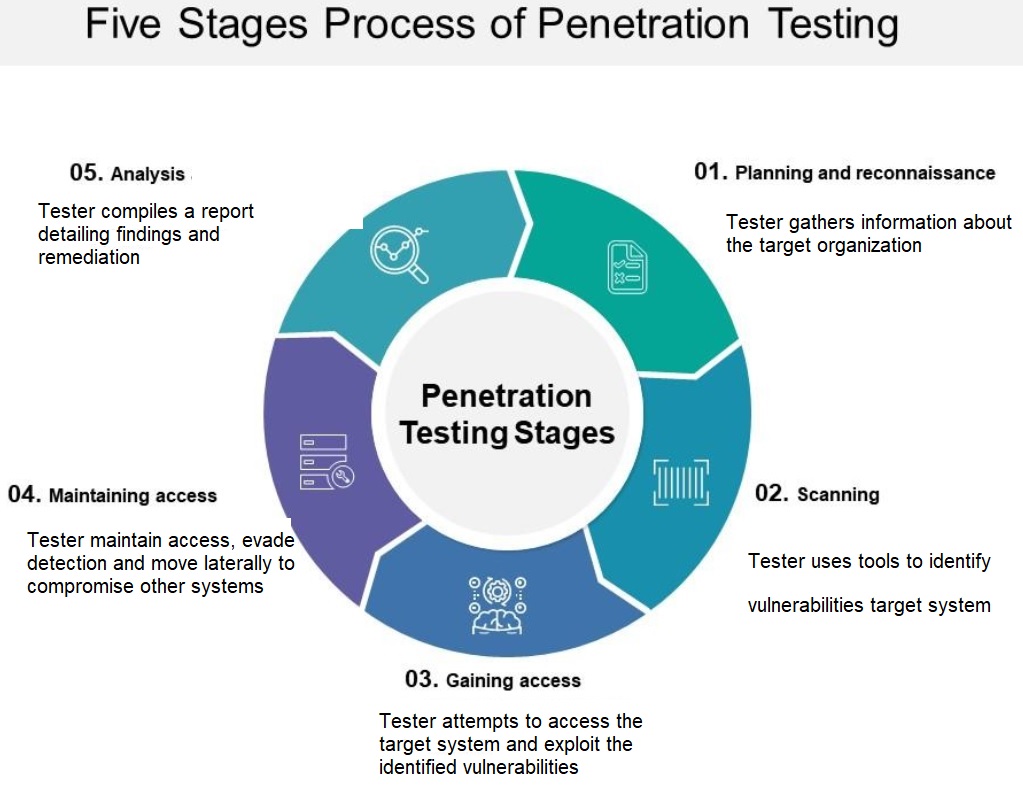
We use MITRE’s ATT&CK framework to simulate attacks. The pen test team will start with the reconnaissance process to discover systems and applications. Then they will continue with scanning and asset mapping in order to identify vulnerabilities for exploitation. Once they find a vulnerable system or application they will gain access to the network. Then they will attempt to move laterally across the network to obtain higher-level privileges. They will try to compromise additional systems and achieve the objective of the pen testing engagement.
The penetration testing team uses a number of open source and commercial pen testing tools to manually perform tasks in addition to the automated tools. The Tests are designed with the goal of minimizing the risk of disrupting business operations.
The penetration testing can be mostly performed remotely via a VPN connection. Some forms of pen testing such as wireless pen testing, may require a member of the team to conduct an assessment on site.
Offered penetration testing services
Network Penetration Testing Service >
A network test identifies security vulnerabilities in applications and systems in your network. It can be internal or external, black box or white box. It typically follows four stages: reconnaissance, discovery, exploitation, and analysis
External or Internal Test
An external test focuses on the perimeter of your network and identifies any deficiencies that exist in public-facing security controls. It attempts to exploit vulnerabilities by an external user. An internal test the network that lies behind your public facing systems. It assumes an attacker has already breached your systems.
White Box or Black Box Testing
White box penetration testing is where the penetration tester has full knowledge of the network, systems and apps in the test scope. A black box penetration test is performed by an external test with no prior knowledge with the network, systems or application.
Web Application Testing >
Web Application testing is a specialized testing for web applications by identifying and exploiting vulnerabilities. This includes tests such as code injections tests, access control flaws test and testing for any problems with authentication and session management,
Wireless Penetration Testing >
Wireless testing examines all devices connected to the business’s WiFi including laptops, tablets, smartphones, and IoT devices. It involves steps like Wireless Reconnaissance to identify network. Then vulnerability and misconfiguration assessment for wireless access points. Then exploitation and reporting
Social Engineering >
Social engineering focuses on people and processes with attacks like phishing, vishing or impersonation. The aim is to test user’s security awareness. During this type of test, the pen tester team will research the company and use information that is publicly available to conduct these social engineering attacks.