Proactively Manage your cyber risks
Cyber security services that leverage the Power of AI to secure your startup or SMB
We provide cyber security services to safeguard your data and IT Infrastructure from evolving cyber threats accordingly ensure compliance with cyber security standards and privacy regulations.

Our approach for a cyber security program in your organization
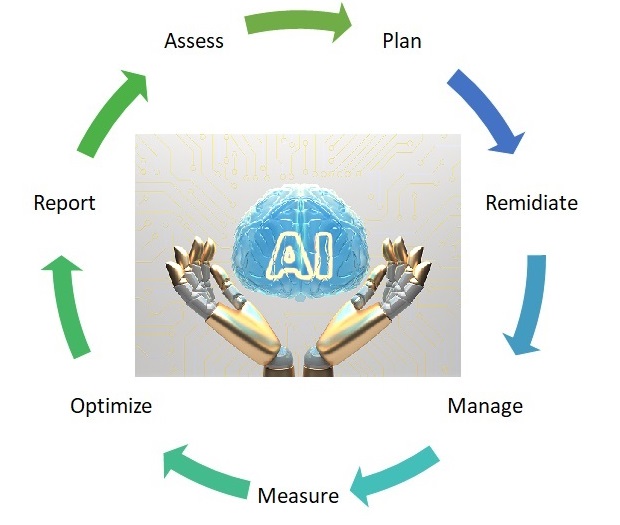
With the assistance of cutting-edge AI tools, we start by:
- Assessing your environment for security gaps.
- Afterwards, we formulate a plan to remediate those discovered gaps.
- Accordingly, we manage plan implementation and measure the results.
- Based on these results we start the optimization process of the implemented security controls.
- Finally, we report and repeat the process. This will significantly increase your security posture
Our cyber security services
We offer a comprehensive suite of cyber security services to protect your IT infrastructure. With the help of our Virtual CISO we help you to achieve compliance and risk objectives. Leveraging cutting-edge AI tools, our approach to cyber security strategy development and risk assessment is unparalleled, ensuring the highest level of cyber security for your organization.
Our Threat Management Strategy
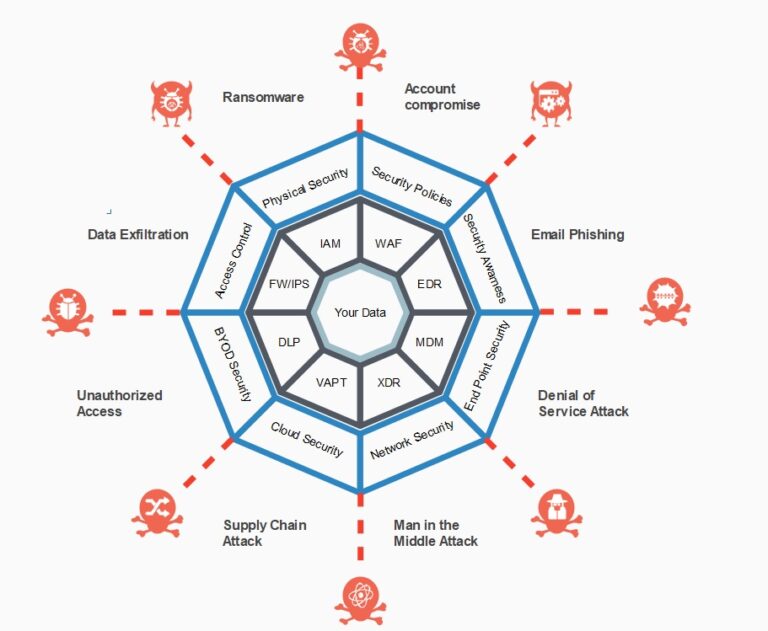
- A detailed analysis of your overall business and your IT infrastructure.
- Assessment of the current cyber threat landscape e.g. Phishing, Data leakage, Ransomware, Unauthorized access, Denial of service attacks, Account compromise …. etc.
- Moreover, we study of your current security controls for adequacy and effectiveness and accordingly identify any missing controls or procedures. Also any violations to the security policy will be identified
- Finally, we provide assistance in selecting, deploying and configuring security controls e.g. DLP, WAF, EDR, MDM, IAM, FW/IPS, XDR, CASB, SIEM, SEG , ZTNA , either on prem, on the cloud or outsourced SecOps as well as any required administrative or physical security controls . Not only this will significantly strengthen your defenses but also increase your protection against threats actors and ransomware attacks.
How can we help you?
Our expertise extends to creating more secure businesses by basically aligning cyber security strategy with business strategy, securing remote or hybrid workforces, and proactively identifying vulnerabilities. Additionally, we excel in addressing privacy regulation compliance, all while providing end-to-end solutions in an evolving threat landscape.
Cyber Security Training
Provide online training for security governance certifications such as CISSP, CISA, CISM, CRISC and CCSP
Cyber Security Strategy Development
Not only we provide cyber security gap assessment but also benchmarking and strategy development
Cyber Security Compliance
Help in compliance with cyber security regulations e.g. HIPPA, SOC 2, ISO 27001, NIST CSF, PCI DSS
Privacy protection
Help comply with privacy regulations both GDPR, and CCPA also any state privacy regulations.
Cloud and Network Security
Help in identifying and mitigating any loopholes in your cloud, on prem or hybrid environment
Help & Support in security incidents
Provide help and support for any cyber security incidents, you may have through our incident response retainer service
On demand cyber security services
Additionally, with our on-demand cyber security services, we provide a diverse portfolio that ensures the protection of your data, no matter where it resides. Our aim is to effectively tackle any cyber security challenges you may come across.




Our Blog
Vulnerability management metrics
Modern Attack Methods on MFA
Zero trust implementation
Generative AI risks in cyber security
Would you like to explore the opportunities with us?
Ocybersec can be your trusted cybersecurity consultant through our Virtual CISO services. Join us in safeguarding your digital assets and IT infrastructure.








