Vulnerability Management Service

Our vulnerability management service ensures that you discover the vulnerabilities that pose the biggest risk to your business and address these risks in a fast and effective manner.
Additionally, the service creates a process for identifying, prioritizing, and remediating vulnerabilities, also it measures and optimize the process for continual enhancements. With our vulnerability management as a service, you can have:
- Visibility and measurement of your assets, threats, and vulnerabilities
- Insights into your infrastructure changes and the impact on your security posture
- Speedy and prioritized patch management of identified vulnerabilities through a change management process.
Benefits of a Vulnerability Management service
- Asset and exposure identification through continuous, vulnerability scanning for the on-premises systems, cloud systems and end points.
- Vulnerability reporting and prioritization by determining which vulnerabilities to remediate first and also the required time frame for remediation.
- Saves you money and time: by having a reliable and managed process with which you can find, and address vulnerabilities present throughout your network.
- Take the burden off of your security team by subsequently offering remote support to address staff shortage.
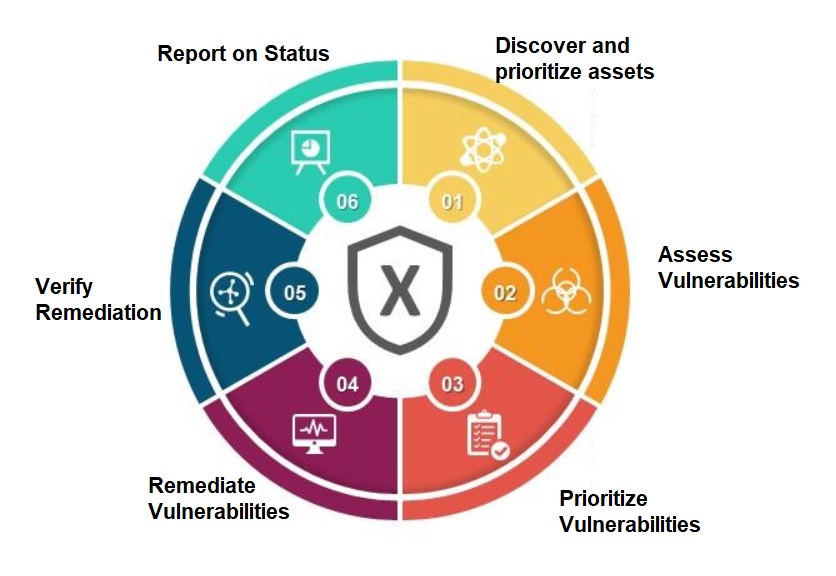
The service includes:
- Discover and prioritize assets: Weekly external and internal network scans to identify new vulnerabilities. We assign each asset a value based on its importance to business operation and role. This helps us knowing its priority and subsequently how urgent is it to fix the vulnerability.
- Assess Vulnerabilities: We do this basically to know state of the applications and systems in their environments.
- Prioritize Vulnerabilities: After the scan, the discovered vulnerabilities will be prioritized based on their potential risk to the business and customers.
- Remediate Vulnerabilities: when we identify and prioritize the vulnerabilities, we mitigate their impact. This is done through effective collaboration.
- Verify Remediation: Once mitigated, verification accordingly ensures a key performance indicator for the process system to ensure it effectiveness and efficiency.
- Report on Status: Reporting on the status of vulnerabilities with reports and dashboards to share with stakeholders.
