Cloud Security Assessment
Assess your cloud workloads against evolving cyber threats with expert services. We assess your cloud security posture across all major cloud platforms, including AWS, Microsoft Azure, Google Cloud Platform, and Oracle Cloud
Methodology
The NIST Cybersecurity Framework’s five core functions (Identify, Protect, Detect, Respond, Recover) as the foundational structure
CIS benchmarks and Cloud Security Alliance CSA guidance for cloud-specific security controls and best practices
- In addition, we use vendor specific security guides such as Azure / AWS / Google cloud security guides when assessing workloads on these public cloud enviroments.
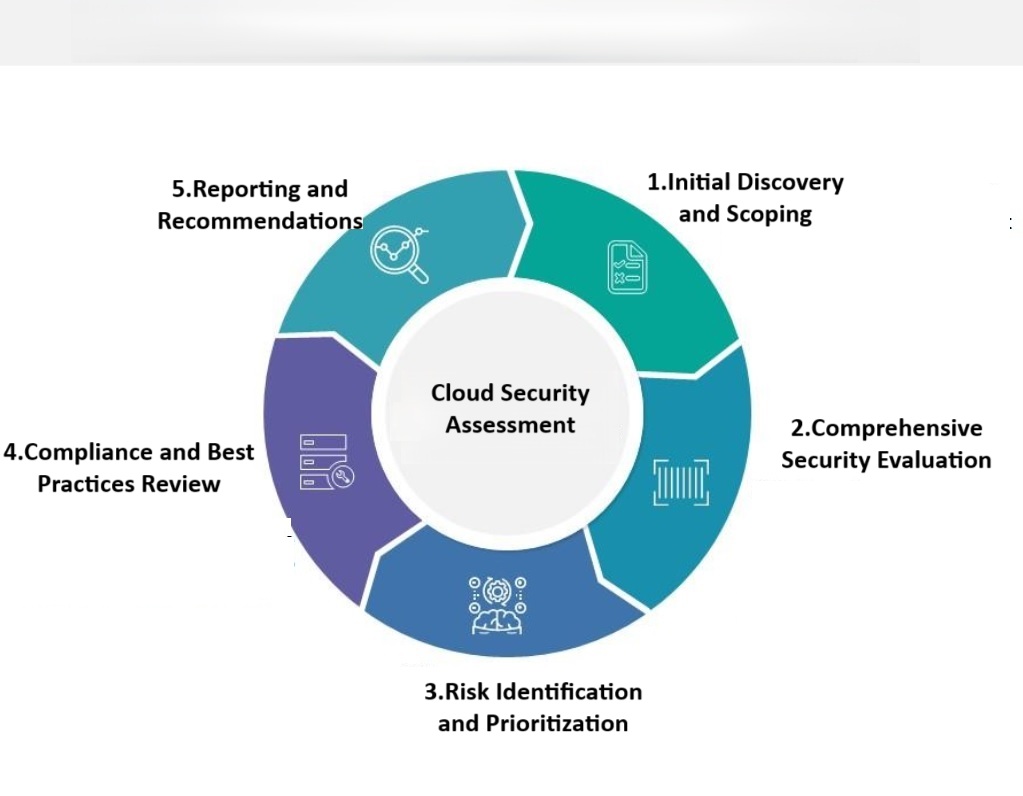
Cloud Security Assessment
Our Cloud Security Assessment empowers your organization to proactively manage cloud security risks, optimize your cloud environment, and safeguard critical data and services from evolving threats
- We begin with a review of your cloud architecture and environment to understand your cloud assets, dependencies, and business objectives.
- We assess your cloud security controls, identity and access management, encryption, network security, monitoring, and compliance posture.
- Our assessment identifies critical security weaknesses, misconfigurations, anomalous behaviors, and potential attack paths, prioritized by severity and business impact.
- We evaluate your cloud environment against industry standards such as NIST, ISO 27001, CIS benchmarks, GDPR, HIPAA, PCI-DSS, and other relevant regulations.
- You receive a detailed, customized report highlighting strengths, vulnerabilities, compliance gaps, and prioritized remediation steps. An executive summary is provided for leadership.
- Ocybersec can assist in designing, deploying, and validating security improvements to strengthen your cloud defenses.
Other key benefits
The assessment will reveal any unintended internet-facing services and applications made by development or Testing teams
The assessment will help to identify vulnerable systems and images in addition to poor configuration practices for data access.
The assessment will uncover gaps in logging and monitoring for security-related events. This will help create a better visibility for security operation whether it is in house or outsourced through an MDR
The assessment will analyze Identity and access management policies and roles which is key in improving your cloud security posture
Advantages & Key Differentiators
- Threat-Informed Approach
- Expert-Led Assessments
- Comprehensive Reporting & Remediation Roadmap
- Multi-Cloud and Hybrid Cloud Expertise
- Alignment with Leading Frameworks and Compliance Standards
- Proactive and Comprehensive Risk Management
FAQ
The assessment supports all major public cloud providers, including AWS, Microsoft Azure, Google Cloud Platform, and Oracle Cloud. We also assess hybrid and multi-cloud environments to ensure unified security across your entire infrastructure.
We begin with a discovery phase to understand your business objectives, cloud architecture, and regulatory requirements. Our risk-based approach ensures that recommendations and remediation plans are customized to your unique environment, priorities, and compliance obligations
Our assessment is designed to be non-intrusive, relying on read-only access, automated tools, and configuration reviews. There is minimum impact on your live services or data, and all activities are coordinated to minimize operational risk.
You will receive a detailed report outlining identified vulnerabilities, misconfigurations, and compliance gaps, along with an executive summary and a prioritized remediation roadmap. We also offer follow-up sessions to discuss findings and support your remediation efforts.
Contact for a project based quote
Contact us to schedule a consultation where we’ll assess your current cloud security posture and manage your cloud risks.
