Cyber security risk assessment
Cyber security risk assessment, is considering the risk a business will be a subject of a security incident that have a negative impact on the confidentiality of sensitive data, or business operations (e.g. ransomware, data leaks, phishing, insider threats malware …etc.)
Organizations perform a cyber-risk assessment to reduce cost of security incidents, saving the organization money and/or reputational damage in the long term. Additionally, it helps the organization avoid regulatory compliance issue and shows stake holders governance concerning cyber risks. It also avoids systems down time and data loss due to a security incident
Our methodology for performing cyber security risk assessment is based on NIST Risk management frame work RMF, NIST SP 800-37, NIST SP 800-53)
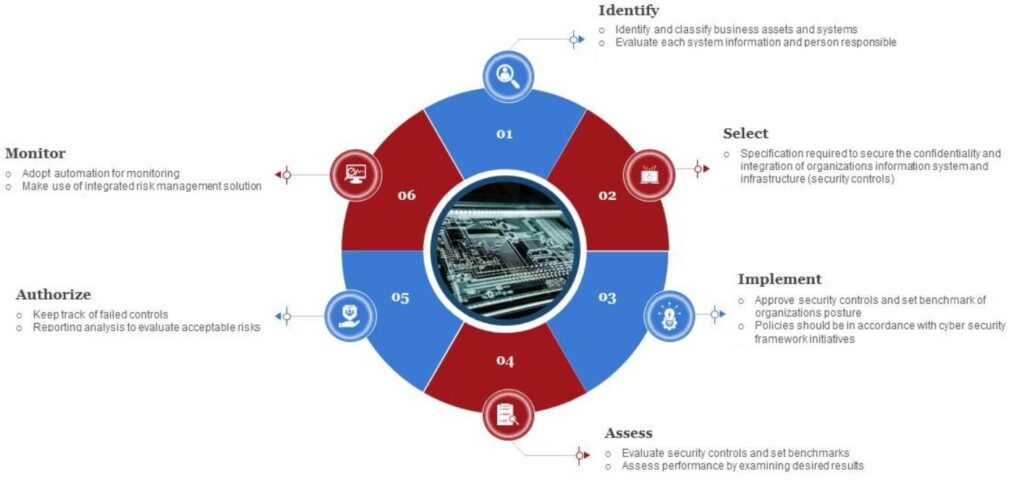
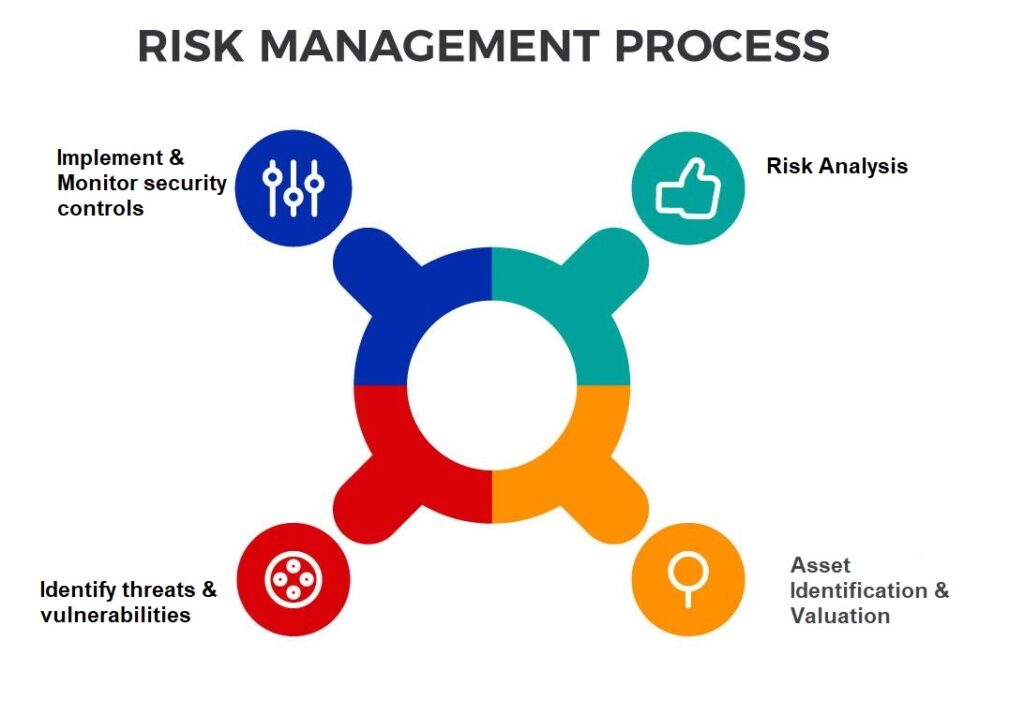
Step 1: Asset Identification and Valuation
After determining the scope, the risk management team must identify the assets that falls inside the scope of the assessment. This include information such as business data, PII data, Intellectual property data. It also includes hardware, software, applications, virtual assets, cloud assets. The risk management team uses a classification scheme to identify value and criticality to business operation.
Step 2: Identify threats and their probability of occurrence.
Threats are typically classified as external or internal, as intentional or unintentional, and also as manmade or natural. Internal man made international threats such as confidential data leakage by internal employee, impersonate another user or use USB to install a malware. External natural threats such as floods, earthquakes and Hurricanes. External man made threats such as cyber criminals. Internal man made threats such as unauthorized access and misuse of information by authorized users
Step 3: Identify vulnerabilities.
A vulnerability is a weakness that a threat can exploit to breach security, harm your organization, or steal sensitive data. Vulnerabilities can be a design fault, a configuration fault, an unpatched system or any other undiscovered weakness. It is also important to identify physical vulnerabilities as an attacker can gain access to a computing system if no proper physical security controls are in place.
Step 4: Risk Analysis
Risk analysis assigns priority to the identified risks and give each one a score based on Probability of occurrence and the Impact on the operation, reputation and financial loss.
For each risk, the risk management team will recommend a response. The response it either accept the risk if the cost of the security controls is more than the loss due to realization of the risk, avoid the risk by discontinue that activity that precipitates the risk., transfer the risk through outsourcing or insurance, or mitigate the risk by implementing a security control. The response depends on the risk appetite of the organization which means how much risk the organization is willing to accept before serious damage to its business occurs.
Step 5: Implement security controls
The risk management team will define and implement security controls for the mitigated risks. Security controls will help you manage potential risks to reduce the chance of them happening Controls are essential for every potential risk. Examples of controls include, Network segregation, encryption, Anti-malware, Multifactor authentication, third party risk management
Step 6: Monitor and review effectiveness
The risk management team in addition to the operation team should monitor the implemented security controls for effectiveness and efficiency. This monitoring will allow those teams to adjust and optimize the implemented security controls. This is basically to cope with the changing threat landscape and the organization business goals.
Cyber security risk assessment lifecycle
Cyber security risk assessment NIST framework