Penetration Testing
Assess your readiness against evolving cyber threats with our expert red team services. We simulate attack techniques used by modern APT to identify vulnerabilities in your security controls. Our comprehensive report provides actionable insights and remediation strategies to strengthen your defenses.
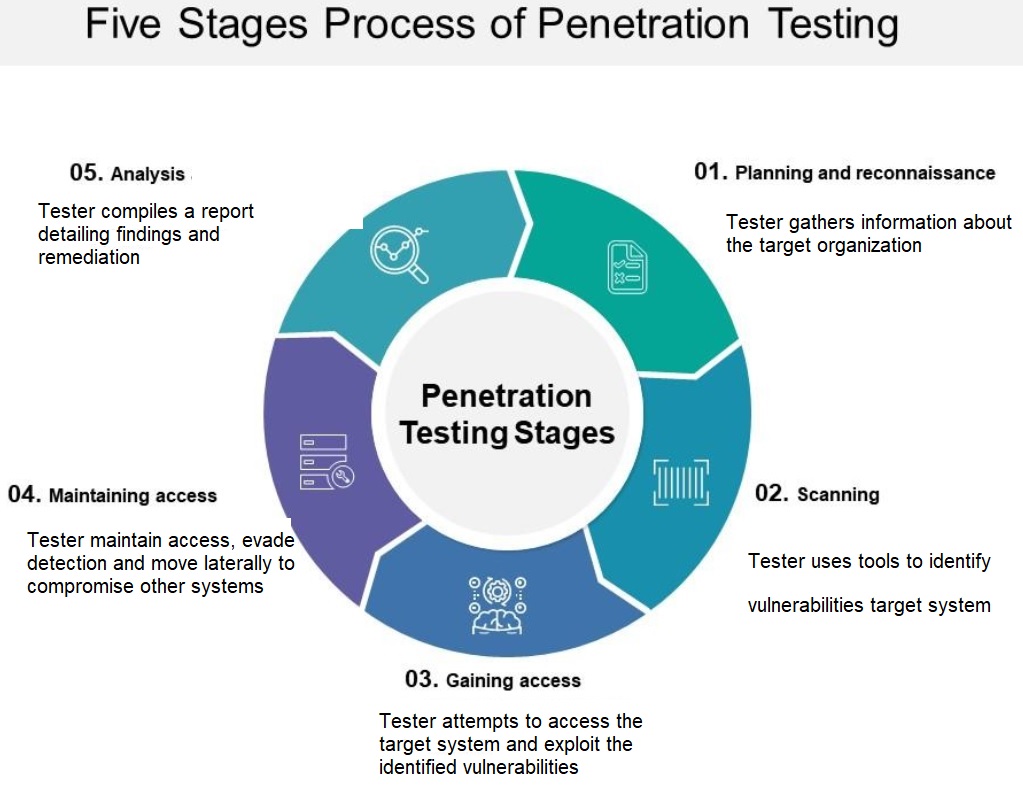
Methodology
Our methodology is based on the Open Source Security Testing Methodology Manual (OSSTMM) which defines the following
- Project scope
- Confidentiality and non-disclosure assurance
- Emergency contact information
- Statement of work change process
- Test plan
- Test process
- Reporting standard
Network penetration testing
Our Network Penetration Testing service follows a structured approach aligned with the MITRE ATT&CK® framework, ensuring a comprehensive evaluation of your network’s security posture against real-world adversary tactics, techniques, and procedures (TTPs). The assessment is conducted in the following key phases:
- Gather intelligence on your network and identify attack entry points.
- Simulate attacks such as phishing and vulnerability exploitation to gain unauthorized access.
- Deploy simulated malicious payloads to test execution within your environment.
- Assess the ability to maintain access using techniques like backdoors and scheduled tasks.
- Attempt to escalate user privileges and extract sensitive credentials.
- Identify weaknesses in access controls and credential management practices.
- Simulate attacker techniques to move across the network undetected.
- Test internal defenses, network segmentation, and access control effectiveness.
- Simulate data exfiltration techniques
- Evaluate the effectiveness (DLP) and monitoring solutions.
- Assess the potential business impact of a successful attack
- Provide a comprehensive report with findings mapped to the MITRE ATT&CK framework.
- Deliver actionable recommendations to strengthen your security posture.
Other key on demand penetration testing services
A specialized testing for web applications by identifying and exploiting vulnerabilities. This includes tests such as code injections, access control flaws test and testing authentication and session management
The service assesses the security of your wireless infrastructure by identifying vulnerabilities in encryption, authentication, and network configurations.
The service evaluates your organization's susceptibility to human-based attacks by simulating real-world tactics. We test employees' awareness and response to phishing, pretexting, baiting, and other manipulation techniques to identify potential security weaknesses.
The service assesses the security of your cloud infrastructure by identifying vulnerabilities. We simulate real-world attack scenarios to evaluate risks related to data exposure, privilege escalation, and misconfigurations across cloud platforms such as AWS, Azure, and Google Cloud
Penetration Testing – Competitive Advantages & Key Differentiators
- Threat-Informed Approach
- Expert-Led Assessments
- Comprehensive Reporting & Remediation Roadmap
- Use of advanced tools used by real hackers
- Customized Testing Solutions
- Support and strategic guidance
FAQ
We offer a range of penetration testing services, including network, web application, mobile application, cloud, wireless, and social engineering assessments. Our tests are customized to fit your organization’s specific needs and security goals.
It is recommended to conduct penetration testing at least every six months or whenever there are significant changes to your IT infrastructure, such as deploying new applications or moving some systems to the cloud.
Our penetration tests are carefully planned and executed to minimize disruptions. We work closely with your team to schedule testing activities during non-peak hours and ensure business continuity while identifying security weaknesses.
After the test, we provide a detailed report outlining identified vulnerabilities, risk levels, and actionable remediation steps. Additionally, our team offers guidance and support to help you address the findings and improve your overall security posture.
We follow strict ethical guidelines and industry best practices to ensure the confidentiality, integrity, and security of your data throughout the penetration testing process. All testing activities are conducted under a signed non-disclosure agreement (NDA), and sensitive information is handled with the highest level of care with strong access controls, encryption and a need to know only.
We offer both.White box penetration testing where the penetration tester has full knowledge of the network, systems and apps in the test scope. A black box penetration test is performed by an external test with no prior knowledge with the network, systems or application.
The duration of a penetration test depends on the scope, complexity, and size of your environment. Typically, a test can take anywhere from a few days to several weeks. We work with your team to establish timelines that align with your business needs and security objectives

