Risk Assessment
Cyber Security Risk Assessment service provides a comprehensive and proactive approach to understanding, evaluating, and mitigating your organization's unique cyber risks. We help you make informed decisions about cyber technologies and solutions, strengthen your defenses, and safeguard your most valuable digital assets
Our approach for risk assessment
We use a systematic process to identify, analyze, and prioritize potential threats and vulnerabilities within your IT environment. Our expert team leverages industry-leading methodologies and cutting-edge tools to provide a holistic view of your security posture
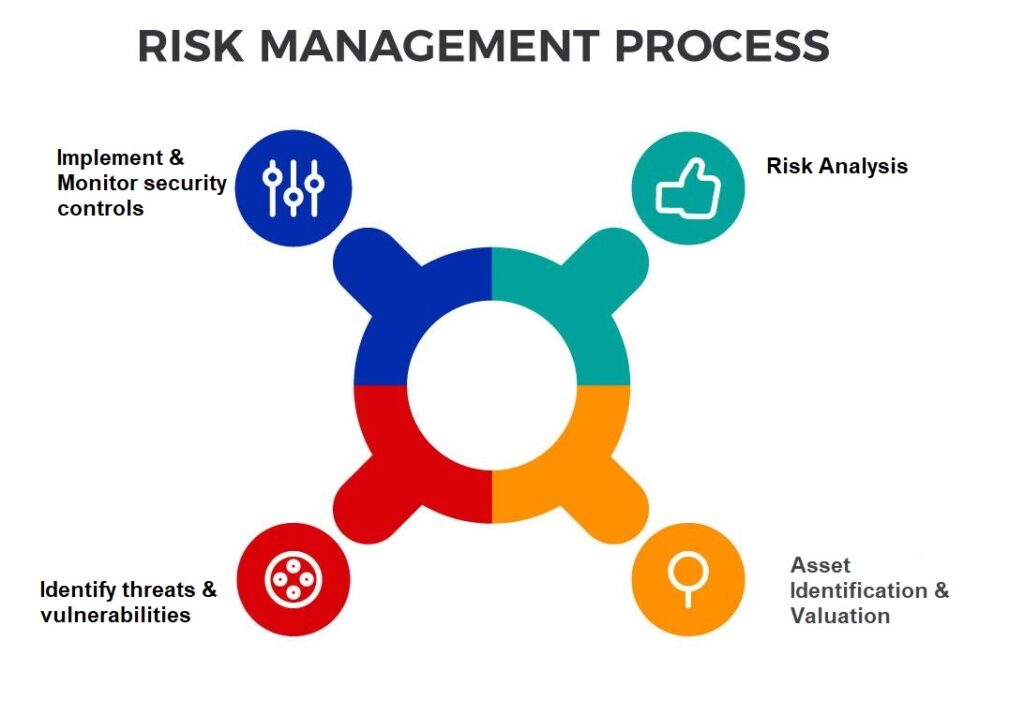
We begin by comprehensively mapping and classifying your critical IT assets, including hardware, software, sensitive data, networks, and applications, based on their business importance and potential impact if compromised.
Our experts identify potential internal and external cyber threats (e.g., malware, ransomware, phishing, insider threats) and uncover weaknesses in your systems, processes, and people (e.g., outdated software, weak configurations)
We assess the likelihood of identified threats exploiting vulnerabilities and the potential impact of such incidents on your business operations, reputation, and financial standing. This includes quantifying risks where possible and prioritizing them based on severity.
We evaluate the effectiveness of your existing security controls and measures, identifying gaps and areas where improvements are needed to meet best practices and regulatory requirements.
Based on our findings, we provide actionable insights and a clear, prioritized roadmap for implementing targeted security measures. This will reduce your risk exposure to an acceptable level and enhance your overall security posture.
We deliver a comprehensive report detailing our findings, risk analysis, and practical recommendations, ensuring clear communication in a simple to understand form for your executive leadership.
- Holistic and End-to-End Approach
- Expert-Driven Analysis
- Cost-Effective Solutions
- Actionable Insights
- Alignment with Business Objectives
Our advantage
At OcyberSec, we differentiate the service through:
Optimized Resource Allocation
Avoid unnecessary spending on security solutions by focusing your budget on the areas that truly matter, maximizing the impact of your cybersecurity investments.
Reduced Financial Loss
Prevent revenue loss, minimize downtime, and avoid the exorbitant costs associated with cyberattacks, such as data breach remediation, legal fees, and reputational damage.
Cost-Effective Approach
We help you avoid wasting time and money on unnecessary security solutions by focusing on the areas of greatest risk and recommending cost-efficient mitigation strategies
improved Business Continuity and Resilience
Develop robust incident response plans and disaster recovery strategies, minimizing operational disruptions and enabling swift recovery in the event of a cyber incident.
Tailored approach
With our tailored approach, we understand the unique needs of startups and SMBs in different verticals, tailoring our assessments and recommendations to align with your specific business goals, growth stage and industry vertical . The process usually lay the groundwork for achieving compliance with a certification such as SOC 2 type II or ISO 27001 to instill customer trust in your products and services
We help you to managing risks, achieve compliance and enhance your cybersecurity posture
The process provide assurance to stakeholders, customers, and clients.
