VCISO
A vCISO service not only more important now than ever but is essential to navigate the complexities of cybersecurity and regulatory compliance. Additionally hiring a full-time CISO can be costly for startups and small businesses. Hence VCISO cybersecurity consulting services offers flexible solution and, in the meantime, a cost-effective approach.
Expert Guidance with fraction of the cost
VCISOs will certainly bring a wealth of knowledge and experience in cybersecurity, providing expert guidance especially for organizations with limited budgets. Additionally, VCISO can
- Assess an organization’s security posture
- Develop strategic security measures
- Provide tailored consulting approach.
Overcome specific cybersecurity challenges
This strategic approach not only enhances the overall security posture of startups and small businesses but also enables them to make informed decisions. These decisions would consequently align with the unique business operational and strategic requirements.
security governance & Compliance
The VCISO will lead the cyber security governance program and will also implement the relevant cyber security framework to your industry vertical.
- SOC 2 type 2
- ISO 27001
- HIPPA & HI Trust
- GDPR & CCPA
- PCI DSS
data security
The VCISO will apply NIST framework for data security to understand, manage and reduce cybersecurity risk accordingly protecting networks, systems and data in a hybrid environment.
- Identify
- Protect
- Detect
- Respond
- Recover
Implementing Cost effective security Controls
The VCISO also understands the constraints and need for cost effective solutions for a startup and SMBs
- Enabling Business through Cybersecurity
- Risk Management: Identification, Treatment, and Mitigation Strategies
- Incident Response Planning
- Security Training and Awareness
- Continuous Improvement
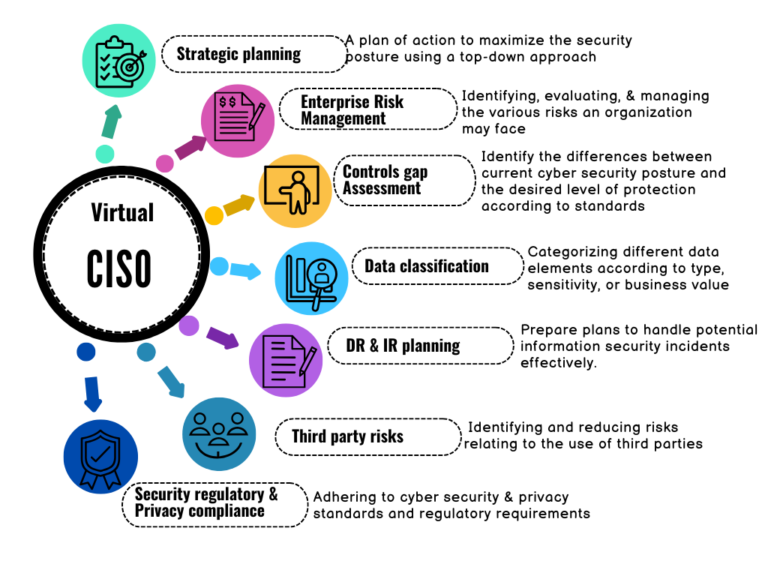
VCISO Responsibilities
- Strategic planning and ensure the alignment of security strategy with business and IT strategy
- Establish cyber security Enterprise Risk Management program
- Security controls assessment, implementation and optimization
- Data classification and protection according to established security policy also implementing data loss prevention solutions
- Incident response and Disaster Recovery planning for your SMB
- Manage risks from third parties e.g. vendors, suppliers and contractors
- Develop security policy and procedures
- Ensure regulatory cyber security compliance (PCI DSS, HIPPA)
- Ensure regulatory privacy compliance (CCPA, GDPR)
Typical results within one year of Vciso service *
Increase in security posture
Security incidents reduction
Compliance with security standards
Strategic security support
Before VCISO is engaged*
After one year of VCISO engagement*
Identify and mitigate key risks in your security posture
The VCISO will initiate, implement and optimize a vulnerability management and penetration testing program with KPIs
Manage risks of working remotely e.g. phishing attacks, malware infections, use of unsecured Wi-Fi networks, unauthorized access
Prepare Incident response and disaster recovery plans for your critical infrastructure. Work closely with the incident response retainer consultant
Evaluating and mitigating any risks introduced by third parties e.g. vendors, suppliers, or business partners
Assess and manage top risks of cloud computing e.g. limited visibility, misconfigurations, data loss, and accidental data exposure
Manage key risks for BYOD usage e.g. data Leakage, Malicious Apps, Device Management Challenges, Device Infection
Continuous monitoring and validation. Least privilege, Device access control, MFA
Proper planning for quick recovery and continuation of services in case of an incident
Once the VCISO is engaged, your security posture should increase significantly within six months to a year from using the service. Afterwards the consultant will maintain and also optimize the implemented security controls. This will accordingly lead to improved governance of your cyber security program
- Cost-effective top-notch service
- Highly experienced and certified consultants
- Focus on challenges of startups and SMBs
- Use of cutting age AI platforms and tools
- Comprehensive reporting
- Guidance on regulatory compliance
- Work closely with your IT or SecOps teams
Frequently Asked Questions for VCISO
A virtual CISO will bring vast experience to your organization without the commitment of full-time employment costs accordingly fulfilling the role with fraction of the cost during a cybersecurity skills shortage.
Virtual CISO services are essentially time-based, and the charge is based on the number of hours per month. Since our Virtual CISO is using AI that basically means you will need fewer consulting hours and higher quality output which enable us to offer competitive pricing
Virtual CISO are generally common across many verticals e.g. technology, marketing, insurance, retail, finance, healthcare, and manufacturing.
We provide committed, experienced consultants with in-depth technical knowledge. Furthermore, The consultants will also use AI and machine learning that give them access to the collective knowledge and experience of world’s best CISO.
Additionally, our consultants adopt a flexible and tailored approach. They work with you to understand your business, how it works and its culture. They will accordingly reflect these unique challenges on their assessment and remediation plans.
The service can use a variety of cyber security frameworks e.g. ISO 27001, NIST CSF, SOC 2 , HIPPA, HI TRUST ..etc. depending on your industry vertical and the maturity of the organization
The Virtual CISO service covers the United States and the EMEA region.
The Virtual Chief Information security officer service will not be responsible for incident response activities. This is the responsibility of the Incident response retainer, nevertheless both the virtual CISO and the IR retainer can collaborate in incident preparedness, post incident analysis review and lesson learned.
The Virtual Chief Information security officer service will not cover day to day security administration function, security monitoring, or incident response activities. This because the service is more of a strategic high-level engagement with a C-level reporting.
The Virtual CISO will effectively communicate the risk of not implementing a security control clearly to executive leadership and relevant stakeholders. This will certainly help in the buy in and streamlining the cyber security program.
For limited resources and budget, the virtual CISO will have to adjust and prioritize. Additionally, frequent communication with stakeholders is key to keep them informed and assist in resource allocation
The virtual CISO will work with the organization to set a risk appetite based on its business goals and objectives. He will implement the security control to reduce cyber security risk to be within the acceptable risk for the organization.
He will also assist the organization to remain productive and resilient without compromising security principles.

Fill the form below to access white paper
AI vCISO Services
Bridging the Gap
A CTO guide

This white paper gives insight about the value driven approach an AI powered vCISO can enhance cybersecurity. Thus, making it a business enabler for the CTO to focus on driving innovation and new services development.
